Nearly half of all data breaches in American organizations involve insiders with authorized access. For CPAs at mid-sized Miami accounting firms, the threat feels personal. Protecting client information from internal risks is now a top compliance concern. This article reveals the hidden dynamics of insider threats in cybersecurity and offers practical steps for safeguarding sensitive financial records while meeting strict regulatory expectations.
Table of Contents
- Defining Insider Threats In Cybersecurity
- Types Of Insider Threats At CPA Firms
- How Insider Threats Compromise Client Data
- Regulatory Standards And Compliance Obligations
- Mitigation Strategies And Detection Methods
- Critical Risks And Liability For CPAs
Key Takeaways
| Point | Details |
|---|---|
| Understanding Insider Threats | Insider threats can be both intentional and unintentional, posing significant risks to client data in CPA firms. |
| Importance of Training | Mandatory cybersecurity training and clear data handling protocols are crucial in minimizing insider threats. |
| Regulatory Compliance | CPA firms must adhere to stringent regulatory standards to protect client information and avoid legal repercussions. |
| Mitigation Strategies | Implementing advanced security measures and fostering a multidisciplinary approach is essential for effective insider threat management. |
Defining Insider Threats in Cybersecurity
Cybersecurity is a complex landscape where the most dangerous threats often emerge from within an organization’s own walls. Insider threats represent a critical vulnerability that can devastate accounting firms and their clients’ sensitive financial data.
An insider threat occurs when individuals with authorized access intentionally or accidentally compromise an organization’s security. These threats can include employees, contractors, vendors, or business partners who possess legitimate system credentials. The danger lies in their intimate knowledge of internal processes and security protocols, which enables them to circumvent traditional defense mechanisms.
Specifically for Certified Public Accountant (CPA) firms, insider threats can manifest in multiple ways. A disgruntled employee might steal confidential client financial records, a careless contractor could accidentally expose tax documents through poor security practices, or an unscrupulous team member might manipulate accounting systems for personal gain. Insider threats increase during workforce transitions and periods of organizational stress.
Pro tip: Implement mandatory cybersecurity training and create clear, documented protocols for data access and handling to minimize insider threat risks.
Types of Insider Threats at CPA Firms
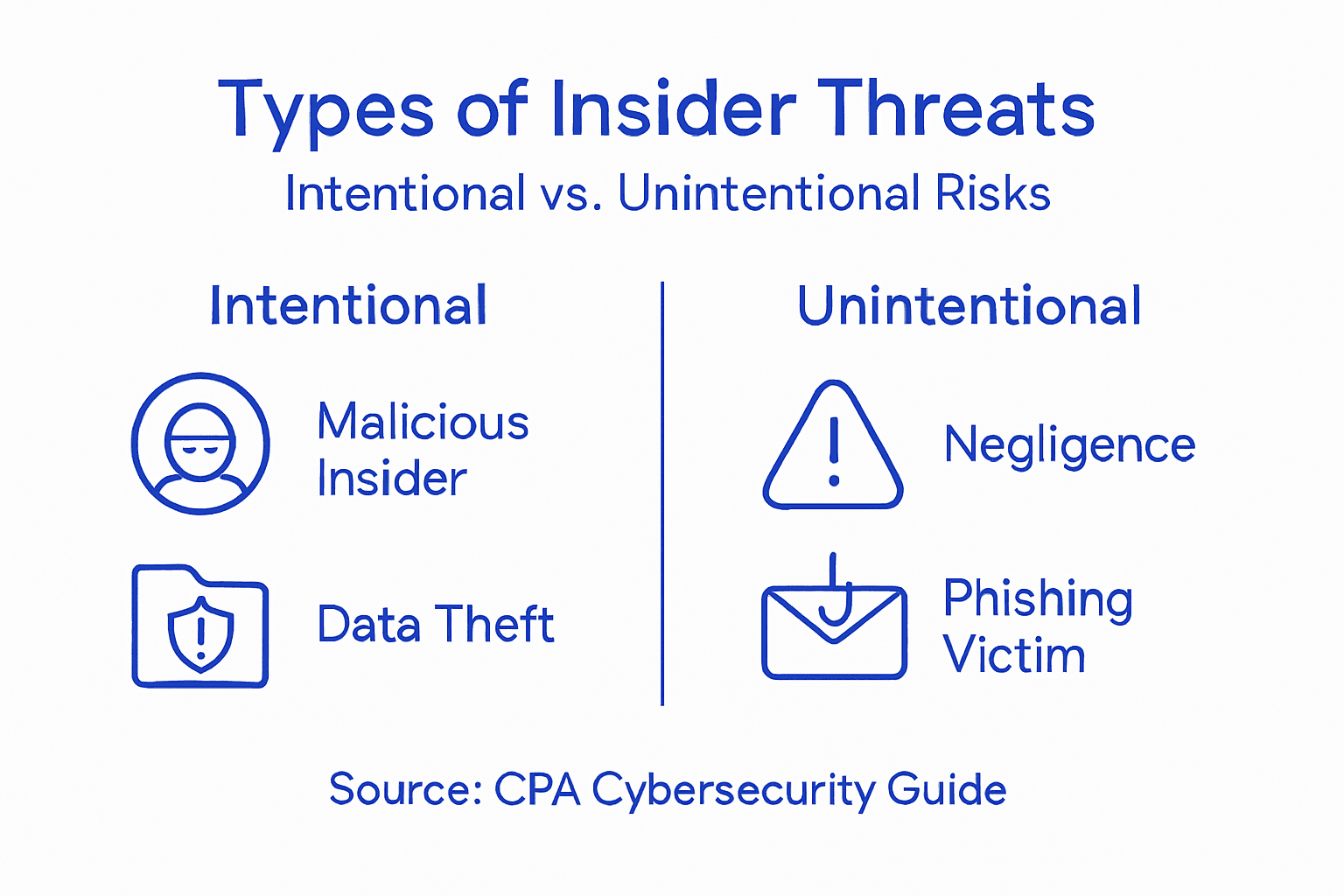
Insider threats in accounting firms are complex and multifaceted, presenting significant risks that extend far beyond simple unauthorized access. Insider threats can be categorized into distinct malicious and negligent types that target sensitive financial information and client data.
The primary categories of insider threats in CPA firms include intentional and unintentional risks. Intentional threats involve deliberate actions like fraud, intellectual property theft, or sabotage, often motivated by personal financial gain, revenge, or ideological reasons. A disgruntled employee might manipulate financial records, steal client data, or intentionally compromise accounting systems to cause organizational damage.
Unintentional insider threats are equally dangerous and stem from negligence or lack of cybersecurity awareness. These threats emerge from workforce transitions and skill gaps in cybersecurity personnel. Examples include accidentally sharing confidential documents via unsecured email, using weak passwords, falling for phishing attempts, or improperly handling client financial information. Contractors, interns, and temporary staff are particularly vulnerable to creating such unintended security breaches.
The following table summarizes the key differences between intentional and unintentional insider threats at CPA firms:
| Threat Type | Typical Motivation | Common Examples | Detection Difficulty |
|---|---|---|---|
| Intentional | Personal gain, revenge, ideology | Theft of client data, system sabotage | High due to stealth |
| Unintentional | Negligence, lack of awareness | Accidental sharing, weak passwords | Moderate, often overlooked |
Pro tip: Develop comprehensive cybersecurity training programs that cover both technical skills and ethical guidelines to reduce both intentional and unintentional insider threat risks.
How Insider Threats Compromise Client Data
CPA firms handle extraordinarily sensitive financial information, making them prime targets for insider data breaches. Insider threats leverage authorized system access to circumvent traditional security controls and compromise confidential client data in ways that are often difficult to detect.
The process of compromising client data typically follows a predictable pattern. Malicious insiders exploit their intimate knowledge of organizational systems, understanding precisely where vulnerabilities exist and how to bypass existing security protocols. They might exfiltrate sensitive tax documents, financial records, or personal client information through seemingly innocuous actions like unauthorized email transfers, downloading files to personal devices, or manipulating database access permissions.
Critical pathways to insider risk often involve complex emotional and situational factors that transform a trusted employee into a potential threat. These pathways might include financial stress, workplace conflicts, perceived professional marginalization, or simple opportunistic behavior. The most dangerous aspect of insider threats is their ability to operate undetected, using legitimate credentials that make their actions appear routine and unremarkable.
Pro tip: Implement robust monitoring systems that track unusual data access patterns and establish clear, granular permissions to limit potential damage from insider threats.
Regulatory Standards and Compliance Obligations
CPA firms operate in a complex regulatory landscape where protecting client data is not just an ethical obligation but a strict legal requirement. International cybersecurity standards provide critical guidance for managing information security and mitigating insider threats across accounting practices.
Federal regulations mandate comprehensive security protocols that go beyond basic data protection. Firms must implement robust controls designed to detect, prevent, and respond to potential insider threats. These requirements stem from various legal frameworks, including securities laws, privacy regulations, and industry-specific compliance standards that hold accounting firms accountable for safeguarding sensitive financial information.
Regulatory obligations require firms to design reasonably effective insider threat management strategies that address both technological and human factors. This means developing comprehensive policies that cover employee screening, access management, continuous monitoring, and incident response protocols. Failure to establish these controls can result in significant legal penalties, loss of professional licensing, and permanent damage to the firm’s reputation.
Below is a comparison of core regulatory measures and their business impacts for CPA firms:
| Regulatory Measure | Purpose | Business Impact |
|---|---|---|
| Employee Screening | Prevents unauthorized access | Reduces insider threat risk |
| Access Management | Limits data to need-to-know | Minimizes data exposure |
| Incident Response Protocols | Ensures quick breach response | Mitigates legal and reputational damage |
| Continuous Monitoring | Detects suspicious activity | Enables real-time intervention |
Pro tip: Conduct annual comprehensive compliance audits that review and update your insider threat prevention strategies to ensure alignment with the latest regulatory requirements.
Mitigation Strategies and Detection Methods
Insider threat mitigation demands a sophisticated, multidisciplinary approach that goes far beyond traditional cybersecurity practices. Insider threat tactics and techniques require comprehensive detection strategies that blend technological monitoring with human behavioral analysis.
Effective mitigation involves creating layered defense mechanisms that address both technical and human dimensions of risk. This includes implementing advanced access controls, continuous monitoring systems, and behavioral analytics that track unusual patterns of system interaction. CPA firms should develop robust authentication protocols, such as multi-factor authentication, privileged access management, and real-time anomaly detection algorithms that can identify potential insider threat indicators before they escalate.
Multidisciplinary teams play a critical role in insider threat prevention, integrating expertise from cybersecurity, human resources, legal compliance, and behavioral science. These teams can develop comprehensive risk identification frameworks that assess employee behavior, monitor potential indicators of insider risk, and create targeted intervention strategies before potential threats materialize. By combining technical monitoring with nuanced human insights, firms can create a proactive approach to insider threat management.
Pro tip: Develop a comprehensive insider threat program that includes regular risk assessments, continuous employee training, and clear escalation protocols for addressing potential behavioral red flags.
Critical Risks and Liability for CPAs
CPA firms face unprecedented legal and financial exposure from insider cybersecurity threats that can devastate their professional reputation and financial stability. Accountants have critical fiduciary responsibilities to protect client data and maintain stringent information security standards.
The potential consequences of insider threats extend far beyond immediate financial losses. Firms can experience substantial legal penalties, professional licensing revocations, and permanent damage to client trust. Regulatory frameworks impose strict liability for data breaches that result from inadequate security controls, meaning CPAs can be held personally and professionally accountable for cybersecurity failures.
Liability risks manifest through multiple channels, including potential lawsuits from affected clients, regulatory fines, mandatory breach notifications, and potential criminal investigations. CPAs must recognize that their professional responsibility includes proactively preventing insider threats, maintaining comprehensive documentation of security practices, and demonstrating due diligence in protecting sensitive financial information.
Pro tip: Develop comprehensive cybersecurity insurance coverage and maintain detailed documentation of your firm’s insider threat prevention strategies to mitigate potential legal and financial risks.
Protect Your CPA Firm From Insider Threats With Strategic IT Solutions
Insider threats pose a significant challenge to CPA firms that deal with highly sensitive financial and client data. Whether intentional or unintentional, these risks demand a proactive approach combining advanced security controls and continuous monitoring to prevent catastrophic data breaches and preserve your firm’s reputation. Understanding the importance of concepts like access management, behavioral analytics, and compliance with regulatory standards is critical for safeguarding your clients and your business.
Take control today by exploring our Security Archives – Strategic IT Consultants For Accountants where we address insider threats head on with tailored cybersecurity solutions designed specifically for accounting professionals.
Don’t wait for a breach to highlight vulnerabilities. Visit Transform42 now to build the cybersecurity foundation your CPA firm needs. Empower your team, secure your data, and scale with confidence knowing all your technology is managed by one trusted partner.
Frequently Asked Questions
What are insider threats in cybersecurity?
Insider threats occur when individuals with authorized access to an organization’s systems intentionally or accidentally compromise security, potentially leading to the theft of sensitive data or breaches.
How can CPA firms identify insider threats?
CPA firms can identify insider threats by implementing robust monitoring systems that track unusual data access patterns, analyzing employee behaviors, and maintaining strict access controls to sensitive information.
What are the different types of insider threats?
Insider threats can be categorized into intentional threats, which involve deliberate harmful actions, and unintentional threats, arising from negligence or lack of cybersecurity awareness among employees or contractors.
What mitigation strategies can CPA firms implement to reduce insider threats?
CPA firms can reduce insider threats by developing comprehensive cybersecurity training programs, employing continuous monitoring systems, establishing robust access management protocols, and creating clear incident response plans.